Fine-Grained Access Control
GuardRails is designed in an opinionated way to ensure that 80% of our users can get immediate value without having to tweak any settings. However, we also understand that large organizations and power users require customizations.
In addition to just working with the repository level permissions from the version control systems, GuardRails now offers fine grained access control.
Permissions can now be granted on the GuardRails level on two distinct levels:
- Users: Permissions on a per-user basis
- Teams: Permissions on a per team and team member basis
Users
The permission for users can be configured in the People menu on the left menu bar.
Once selected, you will be on the Users tab and see a list of all users.
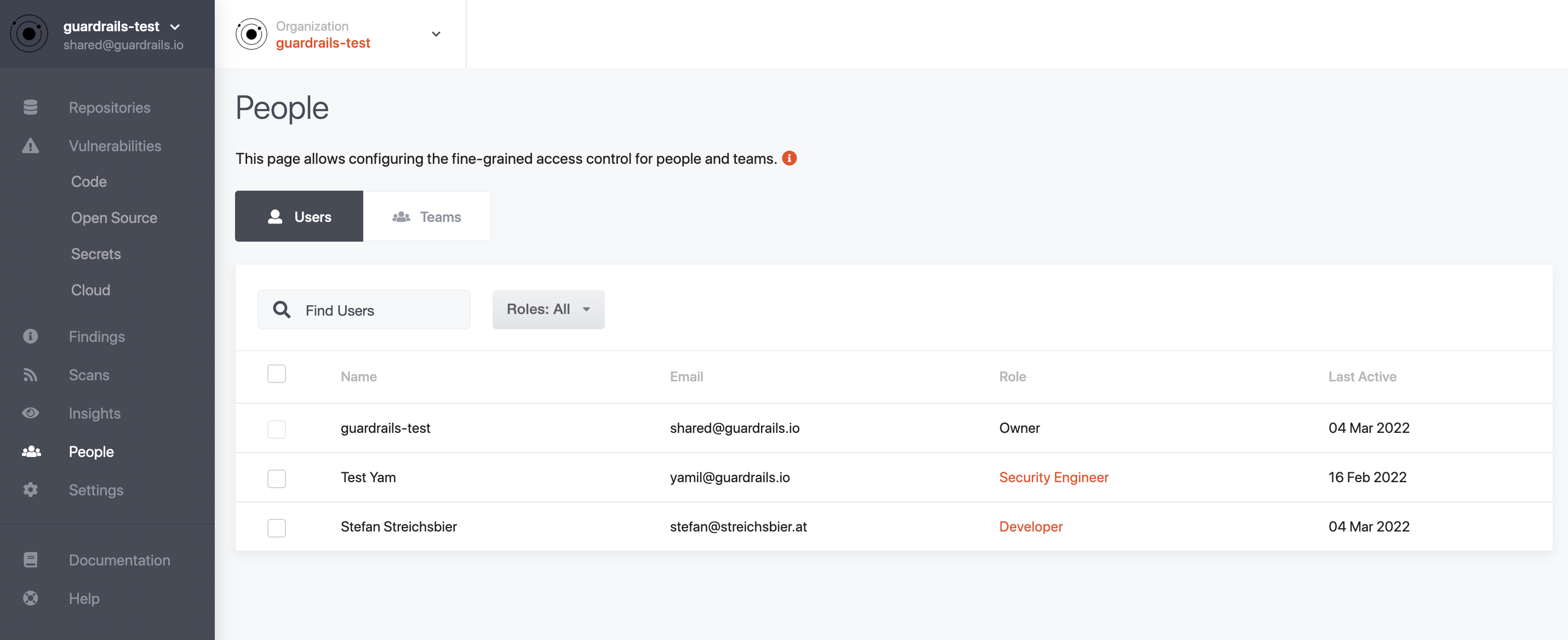
The current user can not change their own permissions, but if they have Manager or Admin/Owner permissions, they can modify the permissions of users. Managers can only set permissions to either Developer, Security Engineer, or Manager. Admins and Owners can change permissions to any role.
Sync all users
GuardRails automatically syncs all organization users from GitHub, including users who have not yet logged in to the GuardRails dashboard. This way, you can pre-configure or manage your users efficiently.
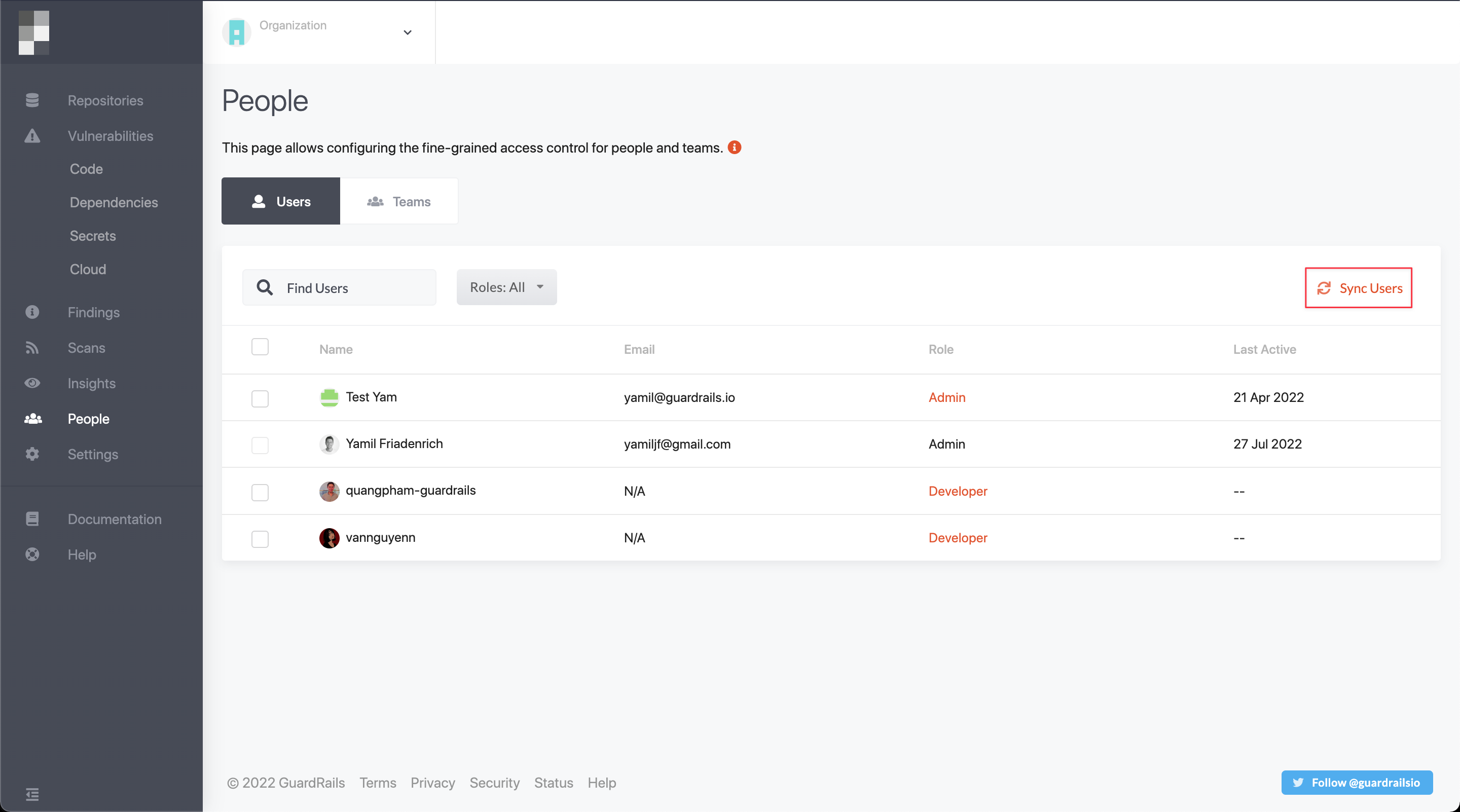
Notes
- The
Sync all usersfeature only supports GitHub withorganizationaccounts.
Teams
The permission for teams can be configured in the People menu on the left menu bar.
Once selected, you can navigate to the Teams tab and see a list of all teams.
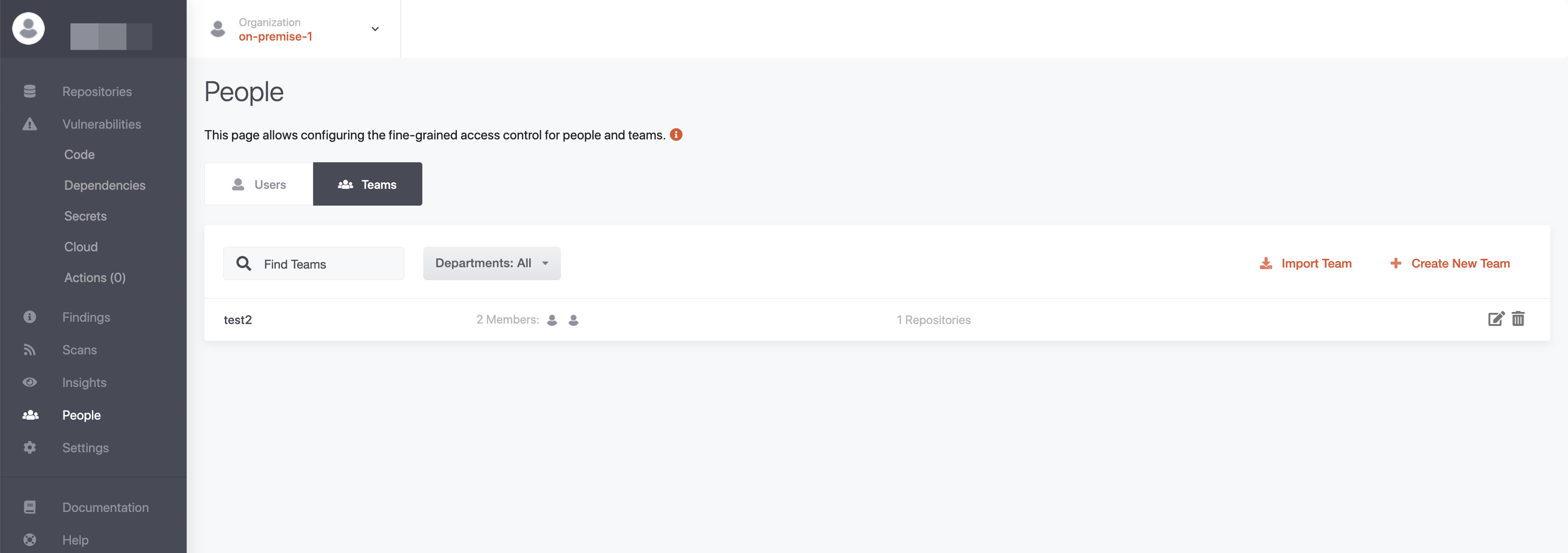
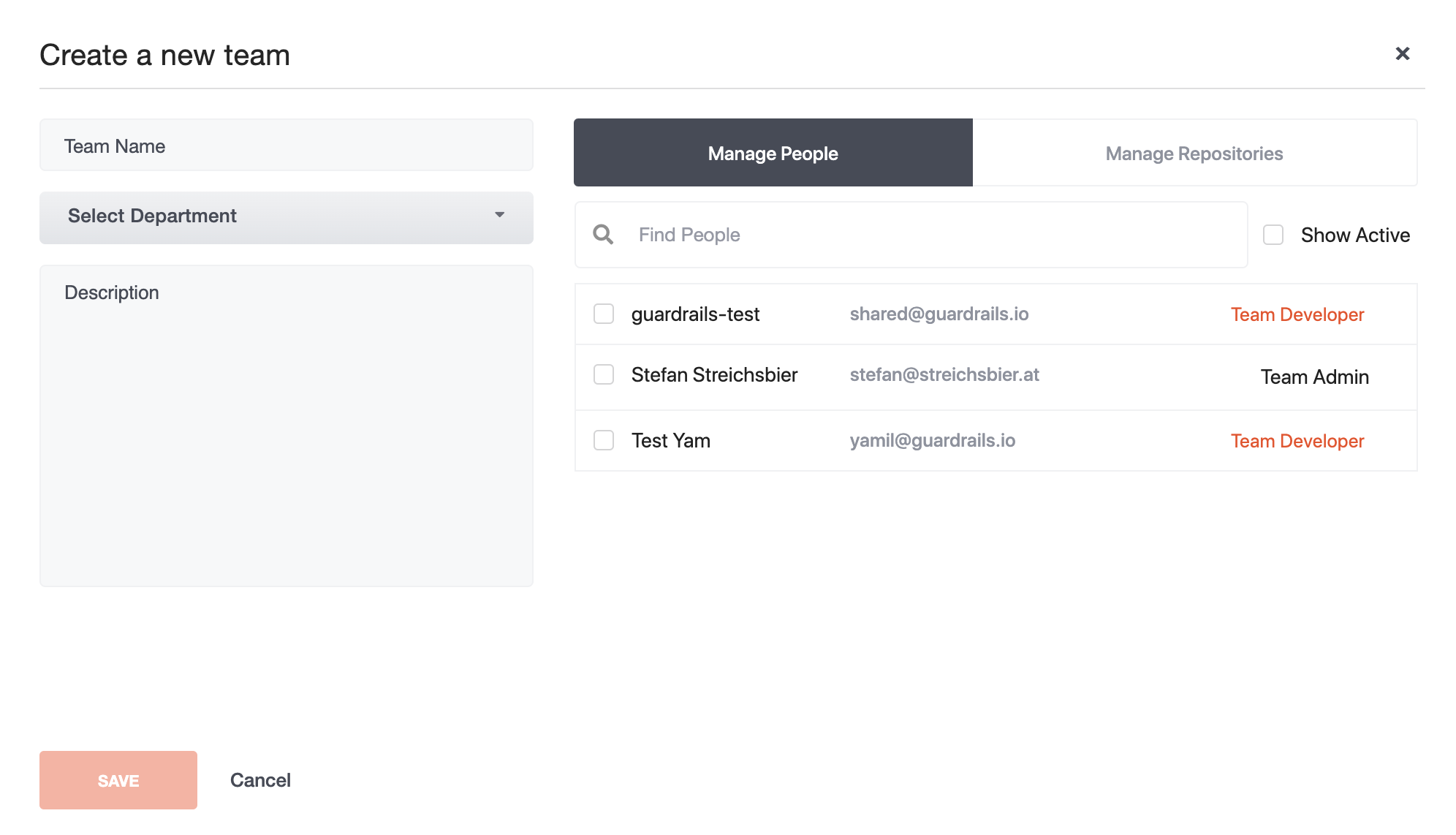
Create New Team
As a Manager, Admin, or Owner you will be able to create new teams and edit existing ones.
When creating a new team, you will automatically become team admin for it.
The following options can be configured:
- Team Name
- Department
- Description
- Which users have access to the team and what their roles are. Roles are either:
- Team Developer
- Team Security Engineer
- Team Admin
- Which repositories the team has access to. Note that users can only add repositories that they have access to.
Import Team
In addition to manually creating teams, you can also import existing teams - the ones that already exist on GitHub - to the GuardRails dashboard. This feature allows you to leverage existing teams and assign custom permissions on it.
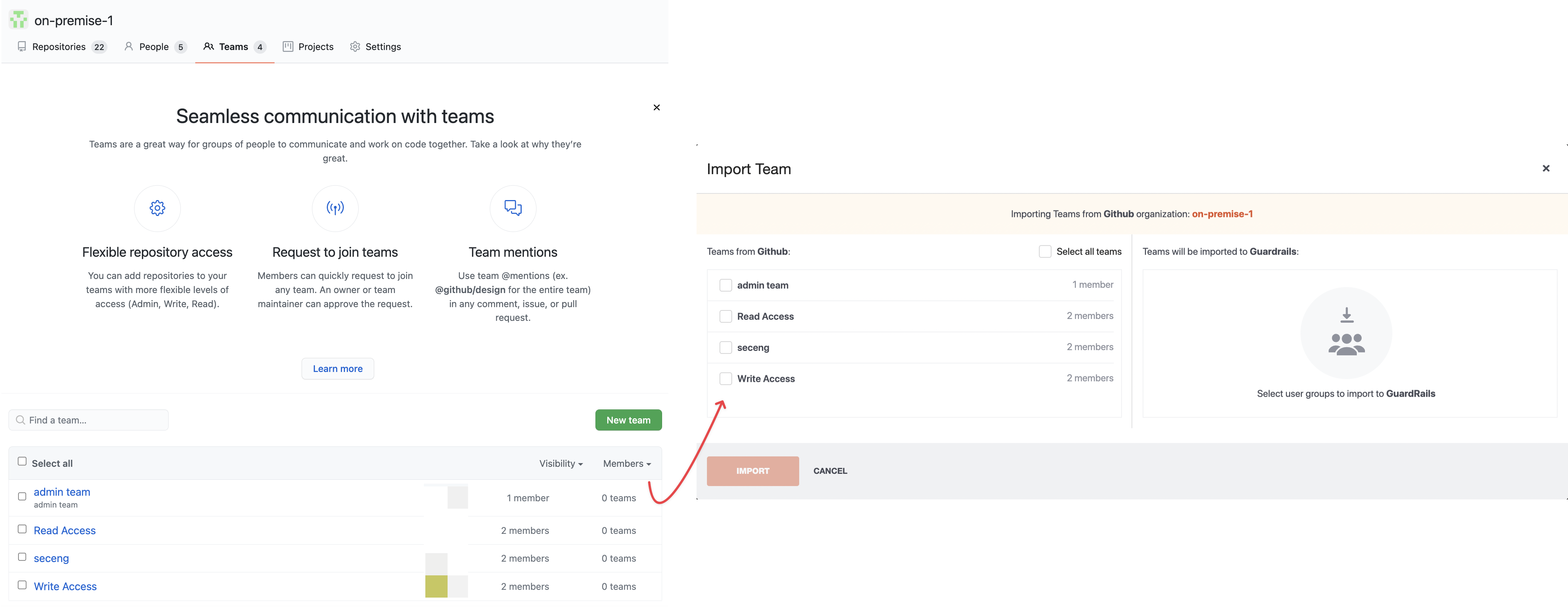
Select the target team(s) and click the Import button to trigger the importing process.
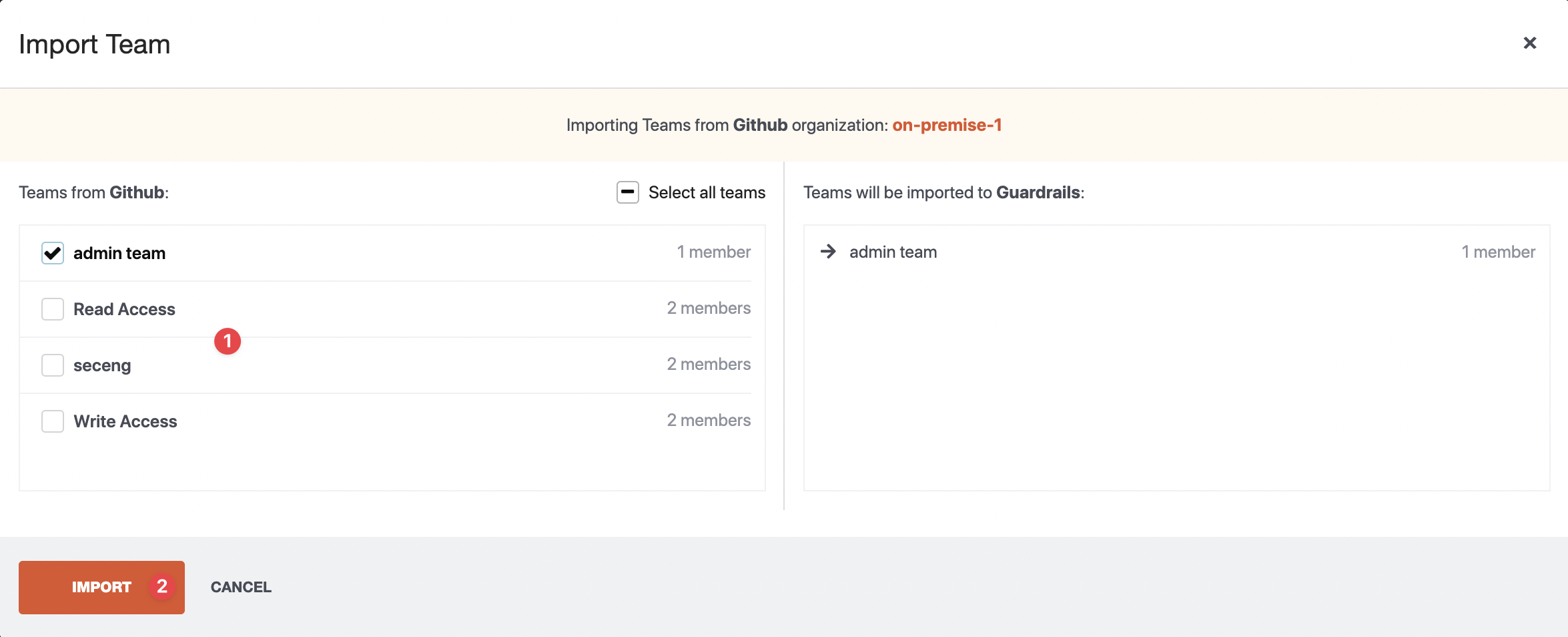
The following information will be populated from the GitHub team:
- Team name
- Members
- Member roles
- Team description
- Accessible repositories
Notes
- The
Import Teamfeature only supports GitHub withorganizationaccounts. - After importing teams, updates will NOT be synced to GuardRails.
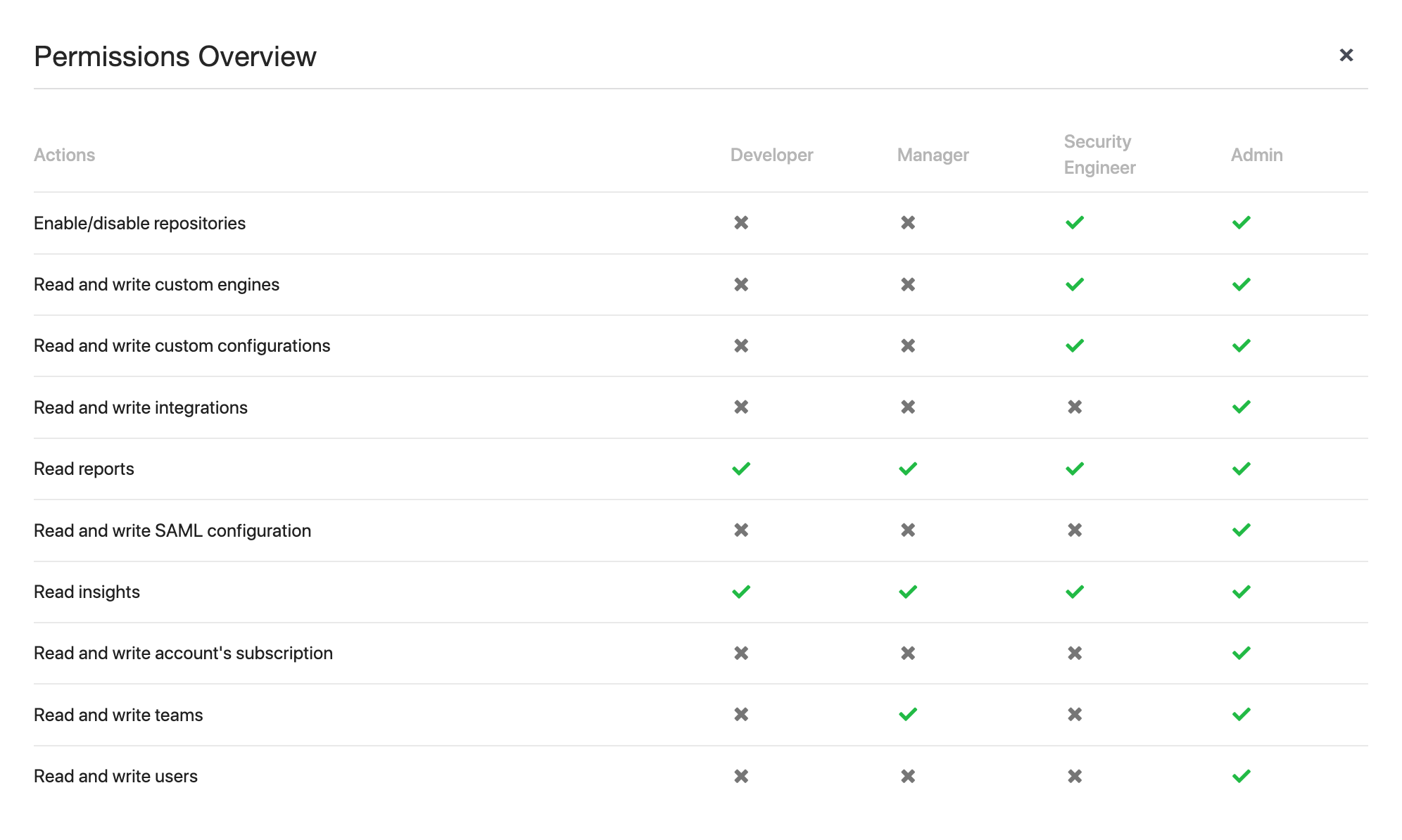
Determining the permissions
The permissions are determined based on the following logic:
- Does the user have access to the repository on the version control level?
- Has the user been given
Security Engineer, orAdminprivileges? - Has the user been given access to the repository as part of a team?