Azure DevOps
Prerequisites
It's simple, all you need is:
- a Microsoft Azure account
Administratorpermissions to create a PAT for an organization
Note: The GuardRails Dashboard is accessible to anyone with access to repositories and groups on Azure. GuardRails uses the Single-Sign-On (SSO) capabilities of Azure.
Getting Started
Start by navigating to the GuardRails Dashboard and click on "Log in with Azure DevOps".
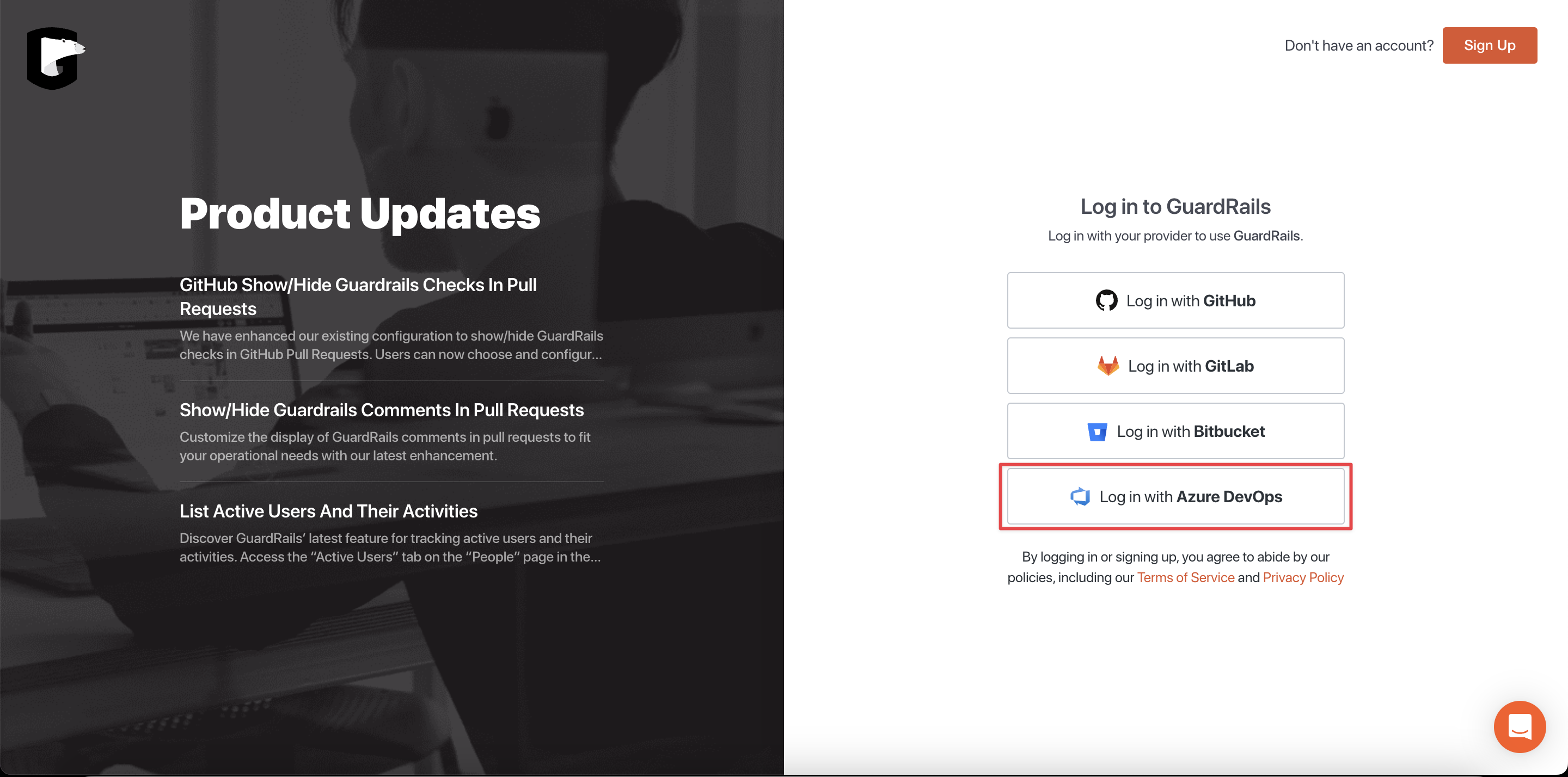
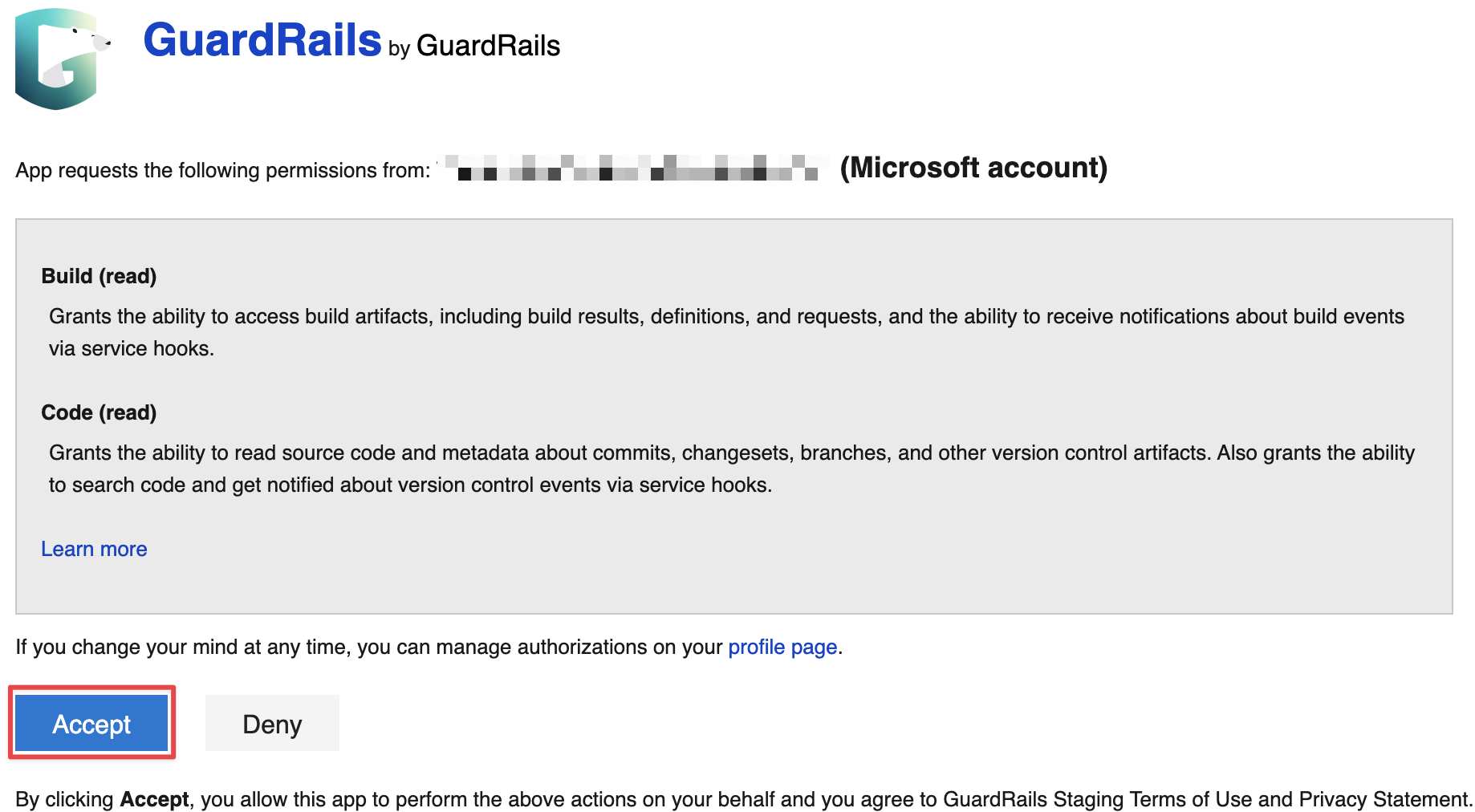
On the next screen, you can review the required permissions and authorize the GuardRails application by clicking "Accept".
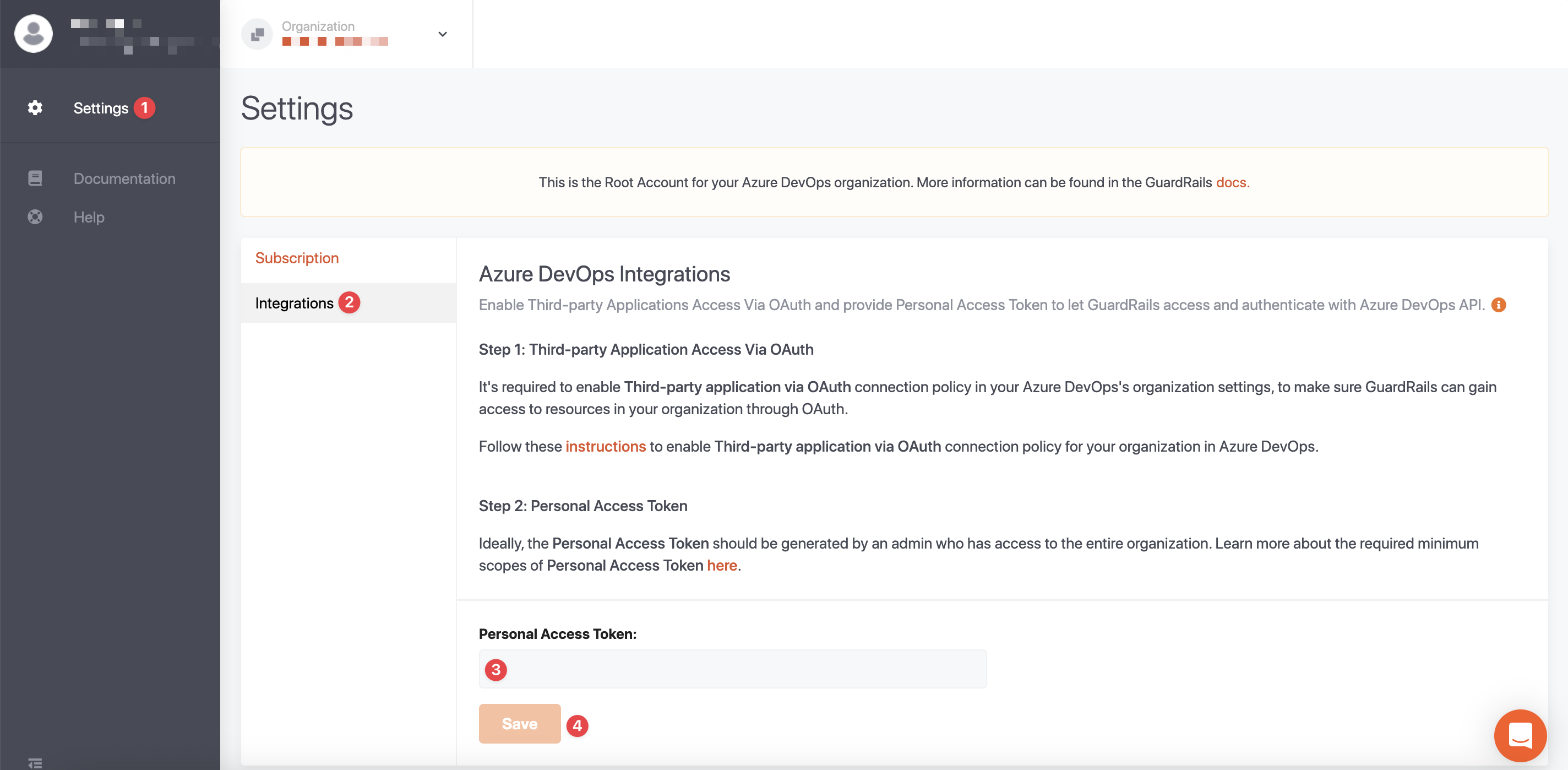
When installing GuardRails into an Azure DevOps organization for the first time, follow the steps below:
1. Enable Third-party Application Access Via OAuth
It's required to enable Third-party application via OAuth connection policy in your Azure DevOps's organization settings, to make sure GuardRails can gain access to resources in your organization through OAuth.
Follow these instructions to enable Third-party application via OAuth connection policy for your organization in Azure DevOps.
2. Synchonize the account
To ensure that the account receives the updated relevant role after enabling Third-party Application Access, it is necessary to log out and then log back in to the GuardRails Dashboard.
3. Create an Azure Personal Access Token (PAT)
The Personal Access Token (PAT) should be generated by an administrator who can access the entire organization, including all projects. It is strongly recommended to generate a PAT for a different admin user per organization to avoid running into rate limit issues. The following scopes are required:
- Expiration: We suggest selecting a token expiration date that is well into the future to prevent any disruption to the integration.
- Scopes: Custom defined
- Build: Read
- Code: Read, Status
- Member Entitlement Management: Read
- Pull Request Threads: Read & write
Once the PAT has been generated, copy & paste it into the GuardRails Dashboard under the Settings menu for the Organization (Root Account).
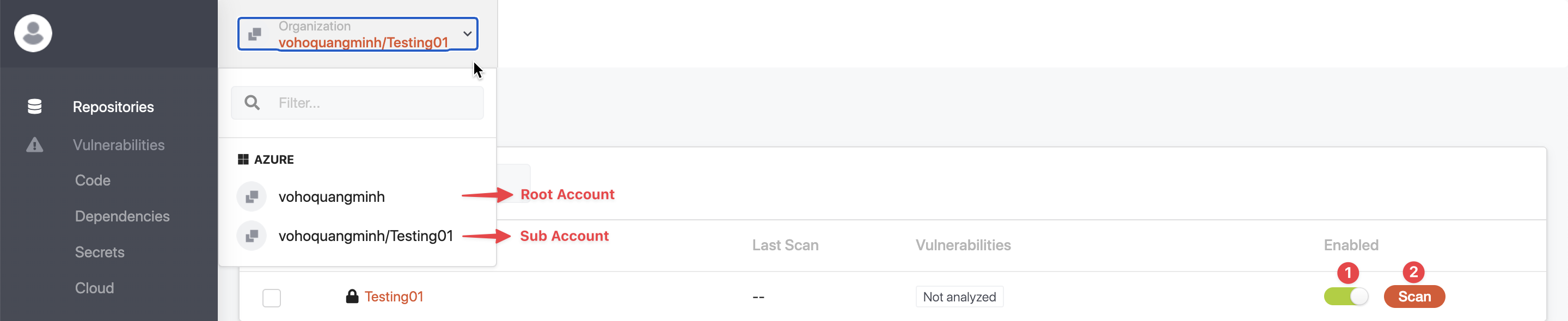
Now, you can navigate to the Sub-Accounts (Projects) and enable the repositories that you want to be scanned by GuardRails, and click on the Scan button next to the enable/disable toggle to start a scan of the default branch of that repository.